Digital Solutions
@Verizon 5G unleashes new possibilities. Stadiums and event venues can reinvent the fan experience with 5G. Check out this video, brought to you by Enterprise Technology International, to find out more about what is possible with @Verizon 5G.
Read MoreConstruction giant #TheWalshGroup gained big with a zero-trust approach to security with @Microsoft #Azure. Read on for more.
Read More@Verizon shares a technology transformation and readiness assessment! Workplaces must transform to accommodate a digital future. This white paper, brought to you by Enterprise Technology International, will show you the steps.
Read MoreThe future is @Verizon 5G. Remote working professionals need the speed, bandwidth, and reliability that comes with @Verizon 5G. Check out this flyer, brought to you by Enterprise Technology International, to see the potential.
Read MoreIdentify and repel security threats with integrated #ThreatProtection from @Microsoft #AzureSecurity and #AzureSentinel. Click here to learn more:
Read MoreFuture Workplace: Business as Unusual. @Verizon shares insights on how remote work trends have grown. Check out this white paper, brought to you by Enterprise Technology International, to learn more about the new remote working normal.
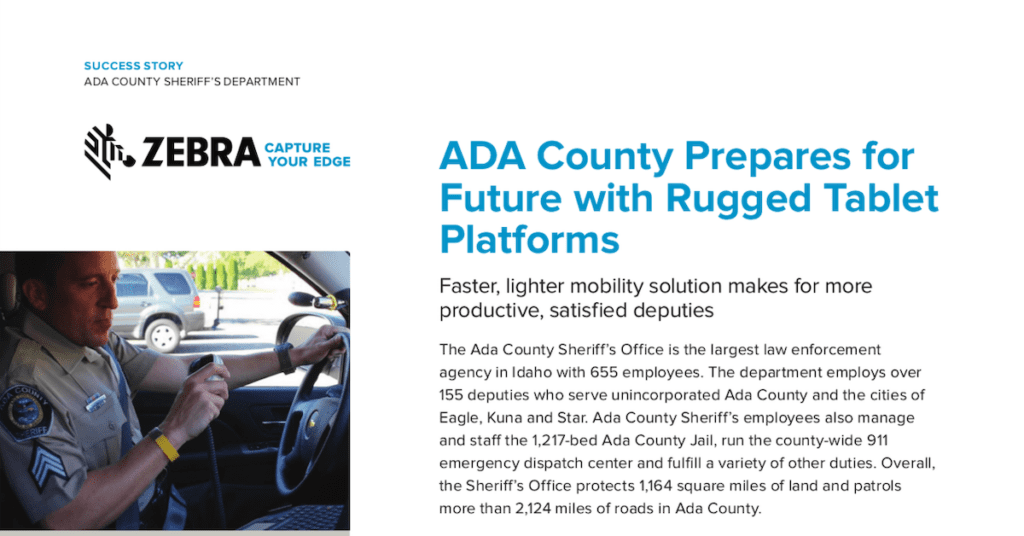
Read MoreThis success story, brought to you by Enterprise Technology International, explains how @AdaCoSheriff replaced its outdated system with @ZebraTechnologies rugged tablets and in-vehicle solutions running on the @Verizon network.
Read MoreIn this spectacular video, brought to you by Enterprise Technology International, IndyCar Champ Will Power uses racing as an analogy to illustrate that edge computing creates lower latency and faster response times. @Verizon
Read MoreThis white paper, brought to you by Enterprise Technology International, states that @Verizon 5G Ultra Wideband is unique because it delivers near-zero latency that provides real-time experiences.
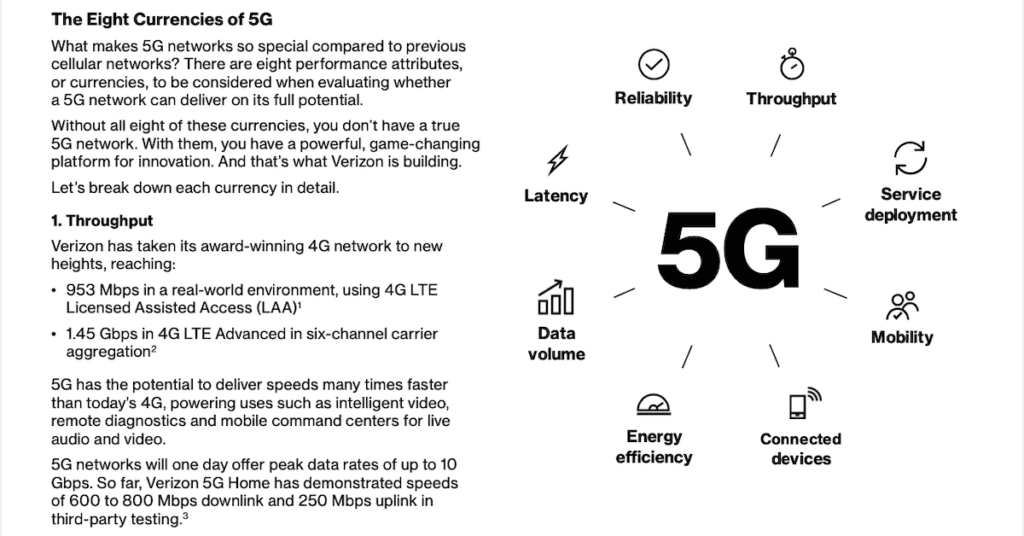
Read More5G vs Wi-Fi 6: deployment considerations for enterprises. This white paper, brought to you by Enterprise Technology International, explains that @Verizon 5G is well positioned to serve most enterprise use cases.
Read More