Digital Solutions
Looking to improve your employees’ remote collaboration? Or maybe you’re not getting everything you want from your video platform? Check out the latest solutions designed to boost remote work productivity. 👇
Read MoreThey go together like a horse and carriage. Of course, we’re talking about your digital transformation and cybersecurity. Read the blog to make sure you get the balance right.
Read MoreDifferent time strokes for different hybrid working folks. The Microsoft blog walks you through some effective #hybridwork time management tips & tricks.
Read More#AI is on the U.S. government’s list of Transformational Cutting-Edge Solutions and is earmarked for some major funding. Read the Thought Leadership piece for additional insight.
Read MoreHow does Microsoft use Red Hat Ansible to automate and standardize processes, improve collaboration and reduce network downtime? Read their story. Contact us to learn how ETI can help you get similar results.
Read MoreIs this the best hybrid work plan you’ve seen?
Read MoreLooking to improve your overall cyber defense posture? Set up a free Cyber Risk Assessment with the experts at ETI.
Read MoreAI is helping the healthcare sector provide more and better care to a larger number of people. AI experts at ETI can help you achieve real data analytics ROI. Schedule an ROI assessment to find out more.
Read MoreHow much can we save you with Microsoft Dynamics 365 Remote Assist? Book an assessment with a Microsoft Dynamics 365 expert from ETI. #MSDyn365
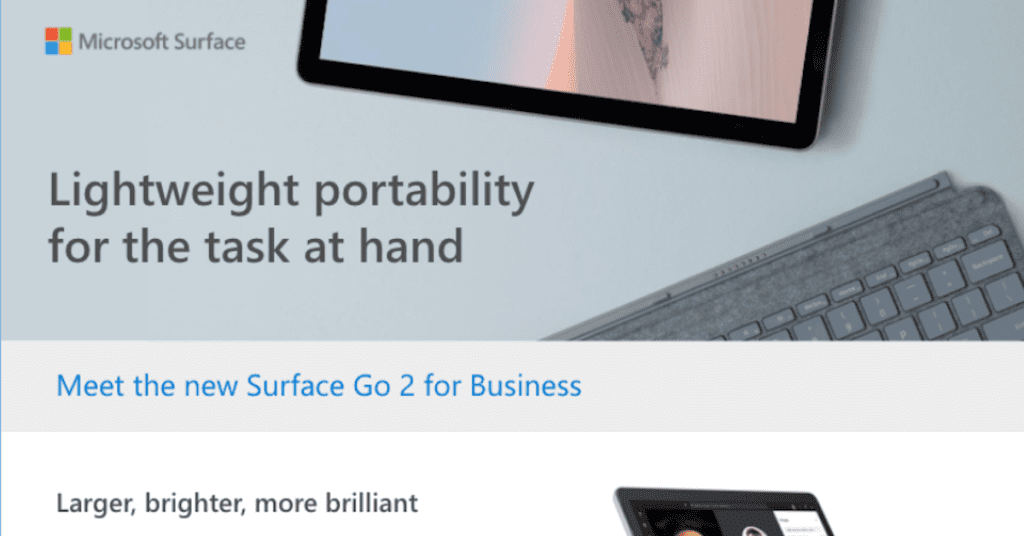
Read MoreMeet the new Surface Go 2 for Business. Microsoft has upgraded the line to deliver even more portability, power, and productivity. It’s perfect for collaboration with enterprise management. Read the facts, brought to you by ETI.
Read More