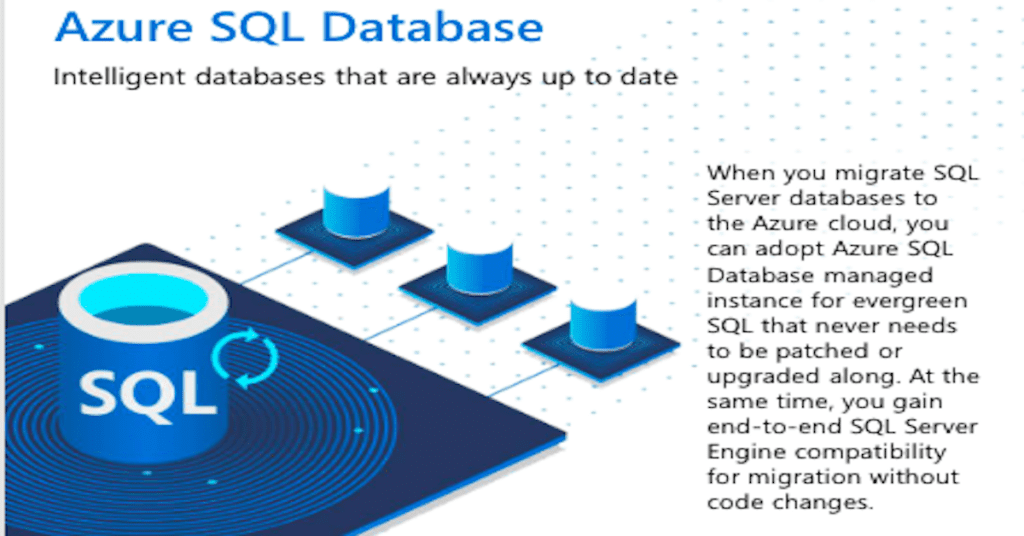
Spend less time on maintenance and more time on creation and innovation when you use #Microsoft #Azure SQL database. Its intelligent databases are always up to date with unique, built-in resource management and governance. Learn more with this infographic:
Read MoreWhy did South Bend Community School Corporation equip its buses with #Cradlepoint NetCloud Service for Mobile and IBR900 LTE routers and deploy them to strategically selected locations during the pandemic? So students and residents could gather near the buses and utilize the Wi-Fi. Read this customer story, brought to you by Enterprise Technology International, to learn more.
Read MoreStrict EU regulations like GDPR make it hard for financial services companies to maintain compliant infrastructures. When GEVA Group’s customers in the finance sector asked for software-as-a-service solutions hosted in the cloud, the Germany-based payment transaction company turned to IBM Cloud. Read this case study to learn why choosing IBM Cloud as a cloud vendor was easy for GEVA Group.
Like and share this post to let us know you found it useful!
#IBMCloud #cloud
Read MoreWith 85% of cyberattacks detected after three months of learning feedback, your business can combine a data-driven, human-guided security approach with the #Microsoft global network. Check out this infographic to see how it evolves with real-time threat intelligence to protect your systems and stay ahead of risks. Contact Enterprise Technology International to learn more!
Read MoreKeep your hybrid work environment protected, and your sensitive data safe with #Microsoft security. Subscribe now and contact Enterprise Technology International to learn more.
Read MoreEmpower your organization to drive innovation and growth with #Azure tools. Explore 3 benefits of modernizing your .NET apps on @MicrosoftAzure with this infographic.
Read MoreTake your app development skills to the next level when you combine serverless computing, AI, and Machine Learning to build intelligence into your applications. This eBook offers a step-by-step guide to help you build and deploy scalable machine learning models with Microsoft Azure.
Read MoreCheck out this solution brief showing what #Dell EMC #PowerStore brings to the table and the many ways it can give your organization the edge by helping you be more agile, improve scalability and reduce costs. Enterprise Technology International can get you started!
Read MoreCybersecurity benchmark study from @CiscoSMB! Check out this video, brought to you by Enterprise Technology International, which introduces research collected from more than 2,800 security and IT decision-makers around the world. You’ll be able to see the top 20 cybersecurity considerations for 2020, and you’ll gain access to the full report, too.
Read MoreWant flexible solutions for elastic scalability, cost savings, and better performance? You can maximize the value of .NET when you use #Microsoft tools and services. Subscribe now to learn more.
Read More