🎱Don’t consult the magic 8-ball for #appdev answers. These 8 reasons for using containers predict success when you combine Microsoft Azure and Red Hat OpenShift. It is decidedly so. 😉
Read MoreTeamwork. Team building. Team collaboration.
We take the need for teams for granted. But there’s another school of thought that questions if we even need teams. 😮 Dive into the controversy 👇
Where is the Federal Government on its journey to deploy EDR technology across devices to track malicious activity? This article highlights progress reported by CISA.
Read MoreWith IBM Robotic Process Automation, accounting firm Deloitte reduced prep time on one management report from 5-8 days to 1 hour and freed up 5 analysts for more high-value work.
How else did they use RPA, and how could your organization put RPA to work to save time and improve efficiency? Read this report. #RPA #automation
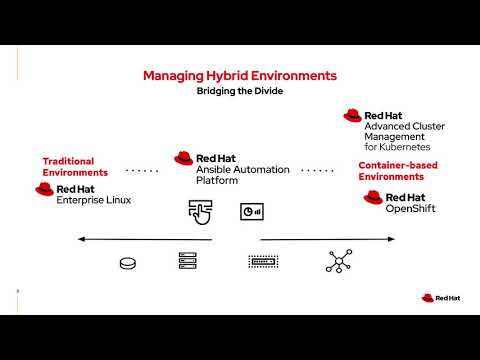
Read MoreWhat can Red Hat Ansible’s Advanced Cluster Management do in hybrid environments? Reduce time and resources, freeing your team up to innovate. Watch this brief demo on ETI’s infrastructure agnostic solution from Red Hat. #RedHat #Ansible #hybrid
Read More👋 Wave if you need a Kubernetes solution that transforms Application development. ETI and Red Hat 👉 point the way forward with OpenShift.
Read MoreThe migration to a more flexible application infrastructure calls for a more flexible firewall. This at-a-glance document, courtesy of ETI, discusses the features of Cisco Secure Firewall Cloud Native.
Read MoreHow do you handle increasingly complex workloads and constantly growing amounts of data while dealing with cost constraints and limitations of legacy storage? It’s quite a juggling act 🤹🏼.
Comment with your thoughts and let us know if you’d like to talk with one of our experts about how we can help. #Dell #PowerStore
Read MoreWhen Sweden tightened security compliance regulations, one of the nation’s leading IT providers struggled to keep up.
Discover how the company ensured compliance and significantly bolstered its security posture by overhauling its cybersecurity platforms and strategy with help from IBM. #cybersecurity #SIEM
Read MoreWebex by Cisco: Collaboration made easy. Review this slide, courtesy of ETI, to learn more.
Read More