ETI
$3.86 million. That’s the average cost of a data breach. Red Hat Insights significantly reduces data breaches and other costly security vulnerabilities. See what makes this solution so unique.👇
Read MoreEnable employees to work in mixed mode—read this essential guide for setting up a hybrid workspace, courtesy of ETI.
Read MoreWhy hybrid cloud? Research shows hybrid cloud generates 2.5 times more value than the adoption of a single cloud platform. Hybrid and multicloud spending is expected to increase up to 17%. Ready to maximize the value of your IT spending? Download this research brief for more data that shows the value of the hybrid cloud. #hybridcloud
Read MoreIs the agriculture sector on the cusp of an #AI-driven transformation? Optimists are hopeful. Read the article to explore the promise and reality.
Read MoreThe value of comprehensive security across all IoT/OT devices can’t be underestimated. What if you could use one solution to secure all your IoT devices and OT infrastructure? With Microsoft Azure Defender for IoT, you can. Watch this video to explore the benefits and get in touch for a demo from an ETI Microsoft Azure Defender for IoT expert.
Read MoreIf you’re wondering if Red Hat OpenShift is really Kubernetes, this eBook will erase any doubts. Get the eBook to discover how Red Hat OpenShift — a 100% certified Kubernetes platform available from ETI — eases the transition to containers. #RedHat #OpenShift
Read MoreAre you looking to elevate your collaborations to a higher level? Microsoft Dynamics 365 offers a clear path to enhanced collaborations when you use Microsoft Dynamics 365 Remote Assist on HoloLens or HoloLens 2. Read the tutorial and DM us to speak with one of our Microsoft Dynamics 365 experts.
Read MoreThe race to hire talent is accelerating. How do you get the top candidates ahead of your competition? Let technology do the heavy lifting 💪🏼.
Read this blog and see if your hiring process could use an automation edge. Reply if ETI can put IBM automation solutions to work for your HR department.
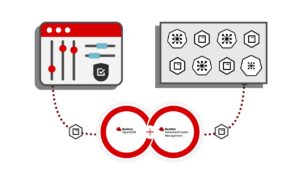
Read MoreIntegration means bridging the gap between existing IT and cloud-based systems. Watch this video to see how Advanced Cluster Management with Red Hat Ansible helps you automate across the enterprise to minimize the time, effort, and risk of modernizing applications. Contact us to learn how ETI can help bridge IT gaps at your organization.
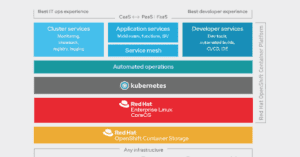
Read MoreWith a Red Hat OpenShift container platform, ETI can help you get the most from cloud-native applications by creating a more agile, service- and API-based development environment that supports continuous delivery and speeds time-to-market. Get this datasheet to learn more.
Read More