ETI
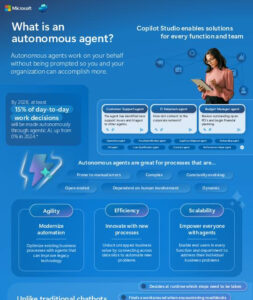
Envision tasks being accomplished without any prompt from you. 🤖 That’s the potential of autonomous agents developed with Microsoft Copilot Studio. These AI-powered agents operate on your behalf without requiring instructions, allowing you and your teams to concentrate on more impactful priorities. Check out this infographic to discover how autonomous agents can convert manual, error-prone tasks into efficient, automated workflows. @Microsoft 365 @Microsoft Copilot
Read MoreWhat is an AI agent, and how can it benefit your business? 🤖 Microsoft 365 Copilot Agents use AI to automate and execute business processes, working alongside or on behalf of people, teams, and entire organizations. Take a look at this infographic to see how agents interact with your data and systems to optimize work, streamline decisions, and enhance productivity. @Microsoft 365 @Microsoft Copilot
Read MoreExplore the power of seamless connectivity with the new Microsoft Surface Laptop 5G. Built for 24/7 access to AI-powered cloud tools, Microsoft 365 and the modern mobile workforce. Contact ETIto order today!
Read MoreSecurity works best when everything works together. 🤝 This eBook, “The Decision-Makers Guide to Comprehensive Security,” highlights how Microsoft brings tools like Defender, Sentinel, Intune, Purview, and Entra together for end-to-end protection. Download your complimentary copy to see how. @Microsoft Security
Read MoreAs #AI adoption grows, security can’t be an afterthought. Microsoft 365 Business Premium with Copilot Business brings AI-powered productivity and advanced security together in one comprehensive solution — so your team can move faster without putting data at risk. With built-in protections for identities, devices, apps, and data — and the option to extend security with Purview Suite — this bundle helps organizations simplify IT, reduce risk, and scale AI with confidence. Download the brochure to see how secure, AI-powered productivity works in practice.
Read MoreUpgrade your productivity game with #Surface 5G-supported PCs. Equip your employees for AI-enhanced work anywhere, anytime. Review the narrative flyer for details and to order the latest Surface Laptop 5G devices, contact ETI today!
Read MoreDon’t miss out on our new content on #Cisco Wireless Wi-Fi 7 APs and its benefits for smarter, efficient, and secure networking environments. Stay ahead with us! Check out this at-a-glance datasheet and contact ETI to get started today.
Read MoreRedefine your productivity with the new #Surface Laptop 5G for Business. Powered by Intel and 5G-enabled for a seamless work experience. Check out this demo video for IT professionals and contact Enterprise Technology International to order today!
Read MoreExplore how Surface Pro can reshape your digital effort. Check out this comprehensive microsite. To order the latest @Microsoft Surface devices with Windows 11 and Copilot+ PC AI experiences, contact ETI today!
Read MoreLean into the future with #Surface Laptop and Surface Laptop 5G. They offer top-notch AI experiences and 5G capabilities, transforming the way you do business. Contact ETI to get started and order new devices today!
Read More